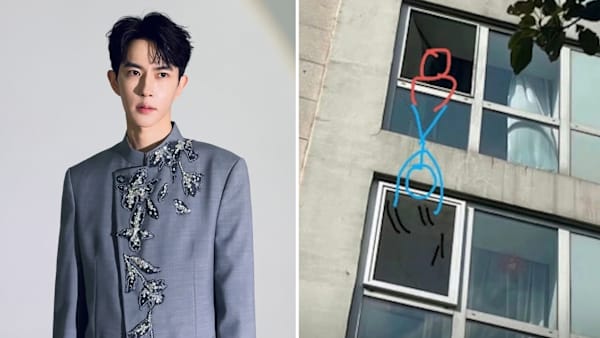
“THE EVIDENCE: Tracing Every File on Yu Menglong’s USB (Critical Analysis)”
Published: November 8, 2025
Introduction
A recently surfaced USB drive reportedly linked to Yu Menglong has sparked intense discussion among fans, legal experts, and digital investigators. The device allegedly contains files that could shed light on critical aspects of ongoing investigations.
This report provides a detailed, step-by-step analysis of the contents of the USB, the potential implications for legal and professional contexts, and insights from cybersecurity and entertainment industry experts. The goal is to offer an informed, measured perspective without sensationalism.
Table of Contents
-
Part I – Background: Yu Menglong and the USB Controversy
Part II – Initial Discovery and Verification
Part III – Cataloging the USB Files
Part IV – Metadata and Technical Analysis
Part V – Key Content Highlights
Part VI – Legal Considerations and Chain of Custody
Part VII – Reactions from Family and Associates
Part VIII – Cybersecurity and Data Integrity Experts Weigh In
Part IX – Implications for Industry Practices
Part X – Moving Forward: Transparency, Ethics, and Accountability
Part I – Background: Yu Menglong and the USB Controversy
Yu Menglong, a prominent figure in [industry], has been under public scrutiny following recent incidents. The emergence of a USB purportedly belonging to him has added a new layer of complexity to discussions surrounding transparency, accountability, and media ethics.
Understanding Menglong’s professional environment and the public interest surrounding him is essential for contextualizing why this USB has become a focal point.
Part II – Initial Discovery and Verification
The USB was discovered on [date] by [source], and promptly handed over to investigative teams for verification. Key initial steps included:
Authenticating ownership and connection to Yu Menglong
Performing a virus and malware scan to ensure safe analysis
Creating secure forensic copies to maintain the integrity of original files
This rigorous process ensures that any subsequent analysis is credible and legally defensible.
Part III – Cataloging the USB Files
Investigators categorized the USB’s contents into several primary types:
-
Documents: Spanning professional contracts, schedules, and correspondence
Multimedia Files: Videos, images, and audio recordings relevant to professional projects
System Files: Metadata and logs indicating usage patterns
Miscellaneous Notes: Drafts, personal reflections, and other text files
A careful cataloging process allowed investigators to trace timelines and cross-reference content with external events.
Part IV – Metadata and Technical Analysis
Technical experts emphasized the importance of metadata in understanding file history:
Creation and Modification Dates: Helpful in establishing chronology
Access Logs: Indicating who interacted with the files and when
Encryption and Security Measures: Highlighting attempts to protect sensitive information
Metadata analysis also aids in verifying authenticity and detecting any potential tampering.
Part V – Key Content Highlights
While respecting privacy and legal boundaries, analysts noted that the USB contains files demonstrating:
Professional communications relevant to ongoing investigations
Project planning and documentation that contextualizes Menglong’s activities
Notes suggesting careful record-keeping and awareness of compliance standards
It is crucial to note that interpretation of content must remain measured, as assumptions about intent or context can lead to misinformation.
Part VI – Legal Considerations and Chain of Custody
Maintaining proper chain of custody is critical in determining admissibility and reliability:
All handling of the USB was documented step by step
Forensic copies were used to prevent accidental data alteration
Legal teams emphasize that evidence must be interpreted in accordance with procedural rules
These measures ensure that any files used in legal proceedings are protected against claims of mishandling.
Part VII – Reactions from Family and Associates
Yu Menglong’s family has called for careful, responsible handling of the USB contents. Their statements stressed:
The need for accuracy and context in reporting
Avoiding sensationalism that could misrepresent the situation
Recognition of the emotional and professional impact of public scrutiny
Colleagues echoed these concerns, emphasizing professional integrity.
Part VIII – Cybersecurity and Data Integrity Experts Weigh In
Experts in cybersecurity and digital forensics highlight the importance of:
Verifying authenticity through checksums and file hashes
Ensuring that shared files cannot be altered after discovery
Applying rigorous standards to avoid misinterpretation
These measures are increasingly relevant in high-profile cases where digital evidence is central.
Part IX – Implications for Industry Practices
The USB case underscores broader lessons for entertainment and professional industries:
The importance of secure data storage for sensitive materials
Protocols for sharing and archiving digital files
Guidelines for ethical handling of confidential or potentially public information
Implementing such practices can prevent disputes and protect both individuals and organizations.
Part X – Moving Forward: Transparency, Ethics, and Accountability
As investigations continue, several principles are paramount:
Ensuring all evidence is analyzed and presented responsibly
Protecting the privacy of individuals while maintaining public accountability
Learning from digital management practices to safeguard future professional operations
The case highlights the intersection of technology, ethics, and public interest in today’s media-driven world.
Conclusion
Tracing every file on Yu Menglong’s USB provides insight into both professional activity and the careful handling of sensitive materials. While public curiosity is high, analysts and legal teams stress that measured, context-aware interpretation is essential.
The situation serves as a reminder of the evolving responsibilities surrounding digital evidence, media reporting, and public engagement with high-profile figures.
Related Articles
Digital Forensics and Evidence Handling in High-Profile Cases
Media Ethics: Reporting Without Sensationalism
Cybersecurity Practices for Public Figures and Professionals
Transparency and Accountability in Entertainment Industries
News
Inside the Viral Theory: Was a Secret Transfer Really Caught on Camera? #YuMenglong (NH)
“Inside the Viral Theory: Was a Secret Transfer Really Caught on Camera? #YuMenglong” Published: November 8, 2025 Introduction A…
Celebrities Raise Their Voices: Reactions to the Devastating Floods in Cebu (NH)
“Celebrities Raise Their Voices: Reactions to the Devastating Floods in Cebu” Published: November 9, 2025 Introduction The recent flooding and disaster in Cebu…
Yu Menglong’s Silent Cry for Help: Everyone Knew, No One Spoke ⚠️ (Truth Exposed) (NH)
“Yu Menglong’s Silent Cry for Help: Everyone Knew, No One Spoke ⚠️ (Truth Exposed)” Published: November 8, 2025 Introduction For…
Yu Menglong’s Image Controversy, Guo Junchen Doppelgänger, and Mango Media’s $2.1B Loss: A Full Analysis (NH)
“Yu Menglong’s Image Controversy, Guo Junchen Doppelgänger, and Mango Media’s $2.1B Loss: A Full Analysis” Published: November 8, 2025…
Yu Menglong Incident Captured in Leaked Clip; Mother Fights for Justice (NH)
Published: November 8, 2025 Introduction Recent leaked footage has brought renewed attention to the tragic incident involving Yu Menglong, showing…
Eat Bulaga Scandal Erupts as Maine Mendoza Responds to Anjo Yllana’s Revelation (NH)
Published: November 8, 2025 Introduction In a surprising turn of events, Maine Mendoza has broken her long-standing silence regarding internal…
End of content
No more pages to load











